WannaCry Success Indicates Complacency In Online Security

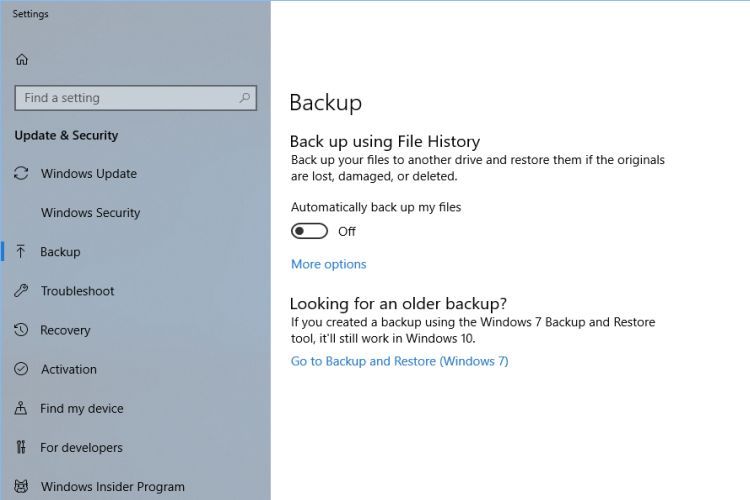
Ransomware is no joke to begin with and this latest immense example has evidently forced a massive number of people to face that reality rather abruptly. The biggest question from a security standpoint is: Why did this even happen? I can think of two good reasons why it should NOT have happened, both of which are focused on standard operating procedures when it comes to maintaining a healthy computing environment. Windows Operating Systems have always had security flaws which ended up having to be patched by Microsoft, sometimes quicker and other times not so quick however the flaw which WannaCry exploited WAS PATCHED by Microsoft last month! Simply following basic online security procedures would have prevented the WannaCry ransomware from infecting a given computer system. The other good reason this should not have happened - especially on the scale that this global infection has occurred - is that if proper backup procedures were followed then the WannaCry infection could easily be eradicated by restoring the most recent (or at least a recent) backup. The only uncertainty there is when the infection actually got in as opposed to when the payload executed. These two factors make it clear that WannaCry success indicates complacency in Online Security.
As latest reports from many news sources (May14 2017) indicate there were some 10,000 organizations and 200,000 individuals in 150 countries infected by WannaCry. That is indeed a massive and evidently successful global attack. How many organizations and/or individuals are actually faced with either paying ransom or losing access to their WannaCry encrypted files is not yet know with precision but if that number is anywhere near the reported number of infections, it is blatant tragedy. It is entirely probable that the majority if not the vast majority of the infected systems need not have been infected to the point of having to pay or lose files at all if basic online security procedures and proper backup procedures were followed. Update Windows, just do it. Back up your system regularly and disconnect the backup device when finished, just do it. Problem solved.
Throughout all of this there some interesting good news because of a cyber security expert known as Malware Tech who found and executed the "kill switch" for WannaCry effectively stopping it. Things could have been worse but they could still be whereas another version of the ransomware is likely on its way. Also worthy of note is the fact that Microsoft actually issued a special update for Windows XP (yes, it's still used) specifically to thwart the ransomware from infecting those systems. If you have a system that has not been properly updated or backed up take those actions immediately! Don't cry and don't be a victim. It's completely avoidable...